In January 2018, an emergency alert sent to local phones informed Hawaii residents of an impending nuclear ballistic missile attack, triggering some understandable panic.
Needless to say, the attack wasn’t real, and a subsequent investigation found that the bogus alert was the result of little more than a clerical error.
But the event prompted researchers at the University of Colorado Boulder to ask the question: How easy would it be to exploit the nation’s emergency alert systems, wreaking havoc on the American public via fake or misleading alerts?
What they found isn’t particularly comforting.
Their full study was recently unveiled at the 2019 International Conference on Mobile Systems, Applications and Services (MobiSys) in Seoul, South Korea. It documents how spoofing the Wireless Emergency Alert (WEA) program to trick cellular users wasn’t all that difficult.
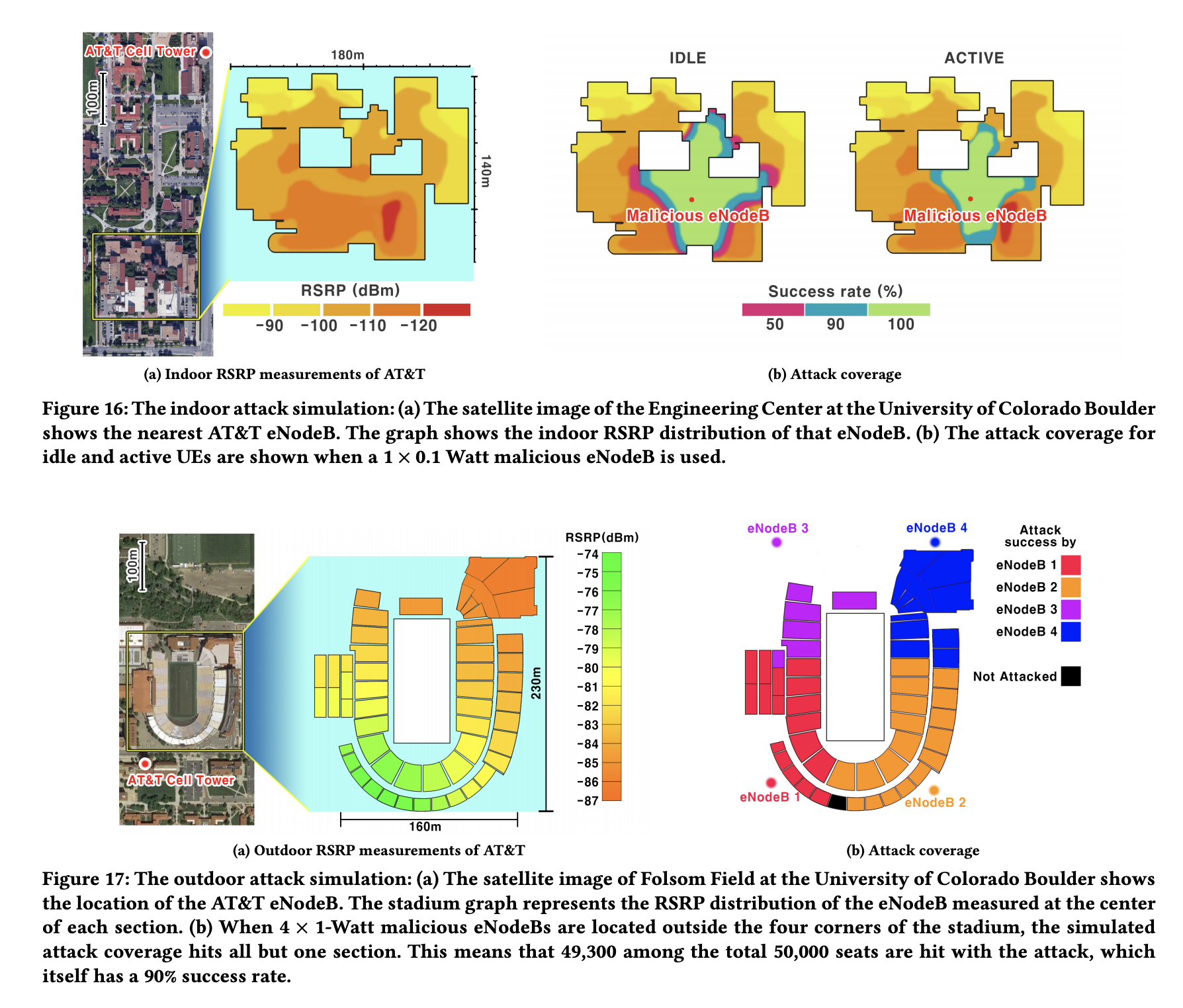
To prove it, researchers built a mini “pirate” cell tower using easily-available hardware and open source software. Using isolated RF shield boxes to mitigate any real-world harm, they then simulated attacks in the 50,000 seat Folsom Field at the University. 90 percent of the time, the researchers say they were able to pass bogus alerts on to cell phones within range.

The WEA system is currently co-managed by both the FCC and FEMA. The system is used to send cell phone users everything from AMBER child abduction alerts to severe weather warnings and—as was first tested last October—Presidential Alerts.
Given these broadcasts’ importance, they’re blasted over a specific cellular LTE channel to maximize reception in geographically targeted areas. But researchers found that it wasn’t particularly difficult or expensive to hijack this process and send out the bogus messages.
The transmission of these messages from the government to the cellular tower is secure. It’s the transmission from the cellular tower to the end user that’s open to manipulation and interference, the researchers found. The vulnerability potentially impacts not just US LTE networks, but LTE networks from Europe to South Korea.
Eric Wustrow, a co-author of the study and an assistant professor in Electrical, Computer and Energy Engineering, told Motherboard such an attack would be relatively inexpensive to fund, fairly simple to conceal, and difficult to defend against in real time.
“We were able to do this attack with commercially-available software defined radios for about $1000,” he said. “The size of our SDR is about the size of a typical wifi router.”
Wustrow told me that attackers might risk being noticed or caught because they’d need to be physically close to their area of attack, “but that's still a large enough area that someone driving through or only sending briefly might escape suspicion,” he says.
The potential for sowing chaos and spreading fear in confined areas like sports stadiums should be fairly obvious. 50,000 users suddenly being warned of a potential attack by nerve gas, for example, would clearly result in some obvious public safety issues.
Wustrow’s team says it has been working with governments and cellular carriers on potential mitigation measures that could help limit the attack’s effectiveness.
He said that using public key cryptography signatures to verify alerts’ authenticity would ultimately prevent this issue, but added that key management would be a complicated mess. Digital signatures verifying the sender’s authority would require each cell phone to have public key, and the authorized government agency to have the corresponding private key.
“This might work okay in the presidential alert case where there's only one or a small handful of parties that would need to have the private key, but wouldn't work as well for AMBER or imminent threat alerts, where multiple jurisdictions and municipalities would need the private key to send such alerts, Wurstrow said.
He added that for a more practical immediate solution, cell phones should only display alerts if they are connected to a trusted cellular network, something that would easily prevent the theoretical attack Wustrow and his researchers demonstrated in their study.
“Ultimately we hope cell carriers, manufacturers, and government entities work together to find a more robust solution,” he says.
DMT.NEWS
via https://www.aiupnow.com
Karl Bode, Khareem Sudlow
