Fueled by rampant employee password reuse across work and personal logins, account takeover represents a major risk to the enterprise. According to the 2019 Verizon Breach Report, the use of stolen credentials has been the number one hacking tactic for three years running. When employees reuse the same credentials across multiple logins, one data breach puts all of those accounts at risk. It’s trivial for criminals to access all accounts that use those compromised credentials, leading them straight into corporate databases and more.
SpyCloud goes beyond detecting compromised passwords; it prevents account takeover from ensuing through the earliest detection possible. SpyCloud Active Directory Guardian automates the identification and mitigation of risk by continually checking on-prem Active Directory and/or Azure AD user accounts against the largest database of stolen credentials in the world. When a match is found, SpyCloud Active Directory Guardian can be configured to automatically reset the password before criminals use or sell them on underground markets. The solution enables you to be proactive in protecting your Active Directory users who reuse passwords.
SpyCloud Active Directory is a browser-based application that runs locally and easily installs in minutes. It can be custom-configured to scan automatically or on-demand.
Key features
- Automated risk detection: Eliminates the manual, labor-intensive process of detecting compromised accounts to help companies protect their assets with fewer costs and resources.
- Early remediation: Gives teams the ability to remediate compromised accounts soon after the initial breach occurs – before criminals have the opportunity to cause harm.
- Credential exposure alerts: Alerts security teams when an Active Directory user account is matched with breach data, enabling a swift password reset.
- Proactive password exposure checks: Enables security teams to proactively check whether any AD user passwords have ever been exposed in a breach.
- Built-in NIST compliance: Helps enforce NIST guidelines across the enterprise by automatically checking AD user passwords against millions of previously-exposed and commonly-used passwords.
- API integration: Enables organizations to quickly integrate SpyCloud breach data into their workflows.
Automated risk detection
SpyCloud Active Directory Guardian eases the burden security teams face when trying to research, parse, normalize and match AD passwords to breach data. The automated solution rapidly and regularly compares active Windows domain users’ credentials against current breach data, on-demand or on a predetermined schedule, encrypting the data for added security. Active Directory Guardian uses native Microsoft calls to pull data from the SpyCloud API and compares it locally to NTML hashes of AD passwords without logging into user accounts.
Early remediation
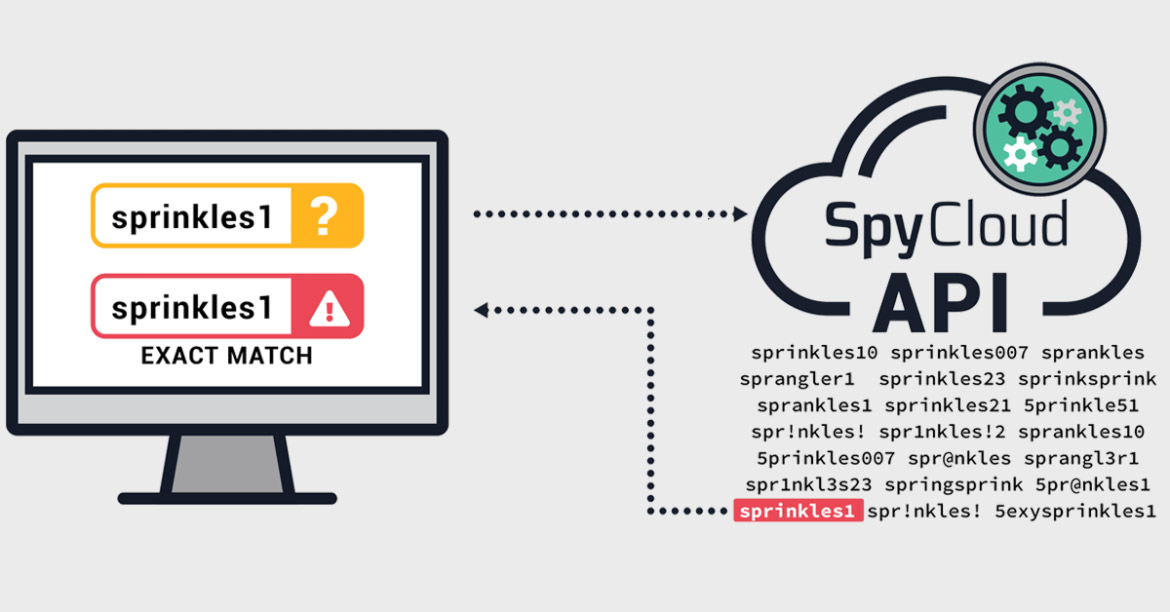
SpyCloud uses automated tools, proprietary tradecraft and human intelligence to find credential exposures early in the breach timeline, before stolen credentials can be used to take over accounts. Dedicated SpyCloud researchers go undercover within underground criminal communities to discover breaches automated tools can’t. If a Windows domain user password (exact match or “fuzzy” match) is found in the SpyCloud breach data, SpyCloud Active Directory Guardian can automatically force exposed users to reset their passwords. Alternatively, you can choose whether the exposure warrants an automatic reset.
Credential exposure alerts
SpyCloud Active Directory Guardian automatically alerts security teams of credential exposures. Within the platform, a dashboard displays affected employee emails, exposed plaintext passwords, and guidance on the type of exposure; for example, the dashboard specifies whether the stolen credentials include an exact match for your employee’s corporate password or a “fuzzy” variation. Whether you choose to run the scan on a regular basis or on-demand, instant alerts provide the necessary insight for rapid remediation.
Proactive password exposure checks
SpyCloud uses proprietary methods to crack recovered passwords at scale, providing them to customers in plaintext. Plaintext passwords make the data more actionable because matches are easy to identify. You can proactively check your AD passwords against this database of plaintext passwords to see whether an employee has reused their AD password, even in combination with different usernames, and if those passwords have ever been exposed in a breach.
Built-in NIST compliance
SpyCloud helps you enforce the latest recommended NIST guidelines automatically. With Active Directory Guardian, you can check for passwords that fail to meet guidelines and put the organization at risk by looking for a match within SpyCloud’s entire database of stolen credentials. If a user chooses a weak or compromised password, the system flags the account and enables security teams to take immediate action.
API integration
You can leverage SpyCloud’s API to rapidly integrate SpyCloud data into your SIEM or user account management tools, enabling you to feed employee breach data into your workflows.
Interested in a free trial? Contact us and give Active Directory Guardian a try today.
Security
via https://www.aiupnow.com
Mirko Zorz, Khareem Sudlow