Networking software giant Citrix Systems says malicious hackers were inside its networks for five months between 2018 and 2019, making off with personal and financial data on company employees, contractors, interns, job candidates and their dependents. The disclosure comes almost a year after Citrix acknowledged that digital intruders had broken in by probing its employee accounts for weak passwords.
Citrix provides software used by hundreds of thousands of clients worldwide, including most of the Fortune 100 companies. It is perhaps best known for selling virtual private networking (VPN) software that lets users remotely access networks and computers over an encrypted connection.
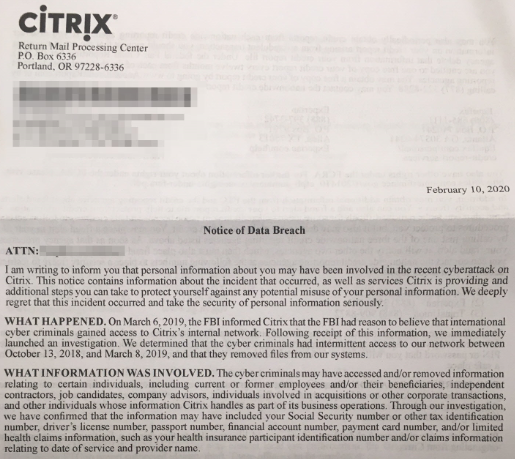
In March 2019, the Federal Bureau of Investigation (FBI) alerted Citrix they had reason to believe cybercriminals had gained access to the company’s internal network. The FBI told Citrix the hackers likely got in using a technique called “password spraying,” a relatively crude but remarkably effective attack that attempts to access a large number of employee accounts (usernames/email addresses) using just a handful of common passwords.
In a statement released at the time, Citrix said it appeared hackers “may have accessed and downloaded business documents,” and that it was still working to identify what precisely was accessed or stolen.
But in a letter sent to affected individuals dated Feb. 10, 2020, Citrix disclosed additional details about the incident. According to the letter, the attackers “had intermittent access” to Citrix’s internal network between Oct. 13, 2018 and Mar. 8, 2019, and that there was no evidence that the cybercrooks still remain in the company’s systems.
Citrix said the information taken by the intruders may have included Social Security Numbers or other tax identification numbers, driver’s license numbers, passport numbers, financial account numbers, payment card numbers, and/or limited health claims information, such as health insurance participant identification number and/or claims information relating to date of service and provider name.
It is unclear how many people received this letter, but the communication suggests Citrix is contacting a broad range of individuals who work or worked for the company at some point, as well as those who applied for jobs or internships there and people who may have received health or other benefits from the company by virtue of having a family member employed by the company.
Citrix’s letter was prompted by laws in virtually all U.S. states that require companies to notify affected consumers of any incident that jeopardizes their personal and financial data. While the notification does not specify whether the attackers stole proprietary data about the company’s software and internal operations, the intruders certainly had ample opportunity to access at least some of that information as well.
Shortly after Citrix initially disclosed the intrusion in March 2019, a little-known security company Resecurity claimed it had evidence Iranian hackers were responsible, had been in Citrix’s network for years, and had offloaded terabytes of data. Resecurity also presented evidence that it notified Citrix of the breach as early as Dec. 28, 2018, a claim Citrix initially denied but later acknowledged.
Iranian hackers recently have been blamed for hacking VPN servers around the world in a bid to plant backdoors in large corporate networks. A report released this week (PDF) by security firm ClearSky details how Iran’s government-backed hacking units have been busy exploiting security holes in popular VPN products from Citrix and a number of other software firms.
ClearSky says the attackers have focused on attacking VPN tools because they provide a long-lasting foothold at the targeted organizations, and frequently open the door to breaching additional companies through supply-chain attacks. The company says such tactics have allowed the Iranian hackers to gain persistent access to the networks of companies across a broad range of sectors, including IT, security, telecommunications, oil and gas, aviation, and government.
Among the VPN flaws available to attackers is a recently-patched vulnerability (CVE-2019-19781) in Citrix VPN servers dubbed “Shitrix” by some in the security community. The derisive nickname may have been chosen because while Citrix initially warned customers about the vulnerability in mid-December 2019, it didn’t start releasing patches to plug the holes until late January 2020 — roughly two weeks after attackers started using publicly released exploit code to break into vulnerable organizations.
How would your organization hold up to a password spraying attack? As the Citrix hack shows, if you don’t know you should probably check, and then act on the results accordingly. It’s a fair bet the bad guys are going to find out even if you don’t.
Networking software giant Citrix Systems says malicious hackers were inside its networks for five months between 2018 and 2019, making off with personal and financial data on company employees, contractors, interns, job candidates and their dependents. The disclosure comes almost a year after Citrix acknowledged that digital intruders had broken in by probing its employee accounts for weak passwords. by: BrianKrebs via https://www.AiUpNow.com/