Academics from École Polytechnique Fédérale de Lausanne (EPFL) disclosed a security
vulnerability in Bluetooththat could potentially allow an attacker to spoof a remotely paired device, exposing over a billion of modern devices to hackers.
The attacks, dubbed
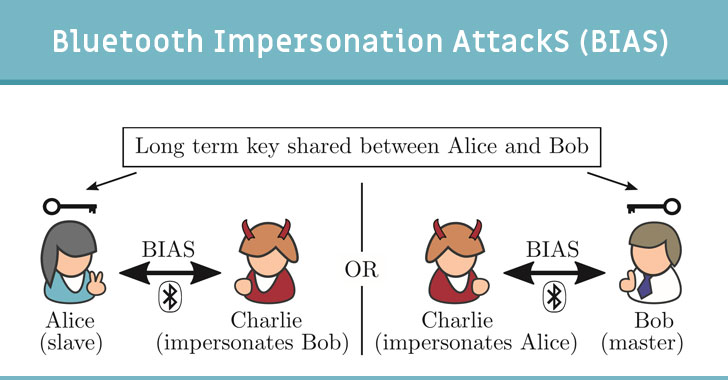
Bluetooth Impersonation AttackSor BIAS, concerns Bluetooth Classic, which supports Basic Rate (BR) and Enhanced Data Rate (EDR) for wireless data transfer between devices.
"The Bluetooth specification contains vulnerabilities enabling to perform impersonation attacks during secure connection establishment," the researchers
outlinedin the paper. "Such vulnerabilities include the lack of mandatory mutual authentication, overly permissive role switching, and an authentication procedure downgrade."
Given the widespread impact of the vulnerability, the researchers said they responsibly disclosed the findings to the Bluetooth Special Interest Group (SIG), the organization that oversees the development of Bluetooth standards in December 2019.
The
Bluetooth SIG acknowledgedthe flaw, adding it has made changes to resolve the vulnerability. "These changes will be introduced into a future specification revision," the SIG said.
The BIAS Attack
For BIAS to be successful, an attacking device would need to be within the wireless range of a vulnerable Bluetooth device that has previously established a BR/EDR connection with another Bluetooth device whose address is known to the attacker.
The flaw stems from how two previously paired devices handle the long term key, also known as link key, that's used to mutually authenticate the devices and activate a secure connection between them.
The link key also ensures that users don't have to pair their devices every time a data transfer occurs between, say, a wireless headset and a phone, or between two laptops.
The attacker, then, can exploit the bug to request a connection to a vulnerable device by forging the other end's Bluetooth address, and vice versa, thus spoofing the identity and gaining full access to another device without actually possessing the long term pairing key that was used to establish a connection.
Put differently, the attack allows a bad actor to impersonate the address of a device previously paired with the target device.
What's more, BIAS can be combined with other attacks, including the KNOB (
Key Negotiation of Bluetooth) attack, which occurs when a third party forces two or more victims to agree on an encryption key with reduced entropy, thus allowing the attacker to
brute-force the encryption keyand use it to decrypt communications.
Devices Not Updated Since December 2019 Affected
With most standard-compliant Bluetooth devices impacted by the vulnerability, the researchers said they tested the attack against as many as 30 devices, including smartphones, tablets, laptops, headphones, and single-board computers such as Raspberry Pi. All the devices were found to be vulnerable to BIAS attacks.
The Bluetooth SIG said it's updating the Bluetooth Core Specification to "avoid a downgrade of secure connections to legacy encryption," which lets the attacker initiate "a master-slave role switch to place itself into the master role and become the authentication initiator."
In addition to urging companies to apply the necessary patches, the organization is recommending Bluetooth users to install the latest updates from the device and operating system manufacturers.
"The BIAS attacks are the first uncovering issues related to Bluetooth's secure connection establishment authentication procedures, adversarial role switches, and Secure Connections downgrades," the research team concluded. "The BIAS attacks are stealthy, as Bluetooth secure connection establishment does not require user interaction."
via https://www.aiupnow.com by noreply@blogger.com (Ravie Lakshmanan), Khareem Sudlow
