As the world becomes increasingly digital, cybersecurity becomes increasingly critical. After serving as the Chief Information Security Officer (CISO) for the New York Stock Exchange for twenty years, Jerry Perullo of Adversarial Risk Management has learned how to protect a company’s digital assets and infrastructure.
Why should you hire a CISO
The first big investment in cybersecurity you should make is hiring a CISO. The primary reason to hire one is that you care about cybersecurity. Your care about cybersecurity can stem from various reasons:
- Altruistic Security: Your company is worried about a potential breach and wants to focus on securing itself and its users.
- Regulatory Requirements: As cybersecurity becomes the norm, every company must maintain specific security standards to comply with the laws and regulations.
- Third-Party Risk Management (TPRM): You want to protect yourself from the liability of failing to protect your clients and customers.
If you’re still wondering whether your company can afford to prioritize cybersecurity, consider the potential cost of failing to.
Key considerations for hiring a CISO
If you’re wondering when you should have hired a CISO, the answer is yesterday. But for companies that haven’t yet, it’s better late than never.
Hiring a quality CISO is a challenge. The first is that they are really expensive. Cybersecurity professionals are already pulling seven-figure salaries in financial services and big tech companies. Even if you find someone under that budget, you must ensure they are a good fit.
As cybersecurity balloons as a field of expertise, the pipeline of young professionals needs time to catch up. While most employee needs eighteen months to understand their product and job function, that can be even more true for CISOs.
Where to Begin: Cybersecurity & Privacy Governance (CyberGov)
CISO can take a long time to get started, but there is still a lot you can get to quickly.
“You don’t have to be a cyber expert to be involved in cybersecurity. On the contrary, you do have to be a businessperson to do a good job of it.”
Put together a Cybersecurity & Privacy Governance committee (CyberGov), and work to bring together everyone who doesn’t come from a cybersecurity background—even if it’s a CFO or a chief medical officer. Over the years, Perullo has developed a handy mnemonic, TRICC, which stands for:
Threats
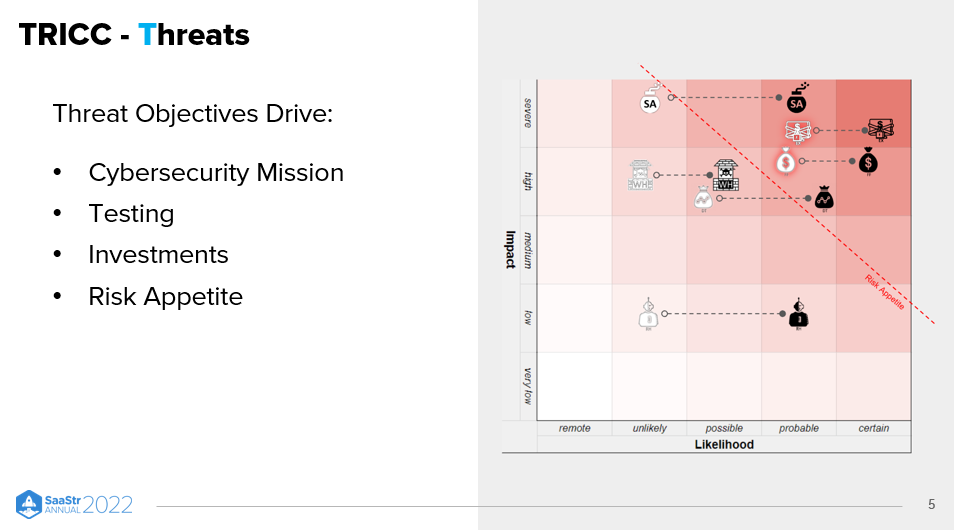
There are numerous threats you can be worried about. To give yourself a clear direction of what you’re up against, you need to be aware of the threats and their impact and prioritize their severity.
“You have to set your mission. Because if you don’t, you’re just boiling the ocean.”
Here’re four drivers you can use to define threats for the cybersecurity committee:
- Cybersecurity Mission. What worries you? What are you fighting against?
- Testing. You may already have seen this in the cybersecurity questionnaires you’ve filled out for your company. Even if you answer 290 out of 300 questions correctly, those ten questions you got wrong may be what you most need to know.
- Investments. For which threat are you most at risk? Examples might include active sabotage (to damage your product), extortion (for example, through ransomware), or fraud. Whatever form it takes, knowing potential motives and objectives can help you organize your investments.
- Risk Appetite. You know best what a regular day looks like in your company and what risks you can comfortably take. But when it comes to cybersecurity, consider bringing in experts to see how these threats might manifest.
Risks: Risk Assessment Management Procedure (RAMP)
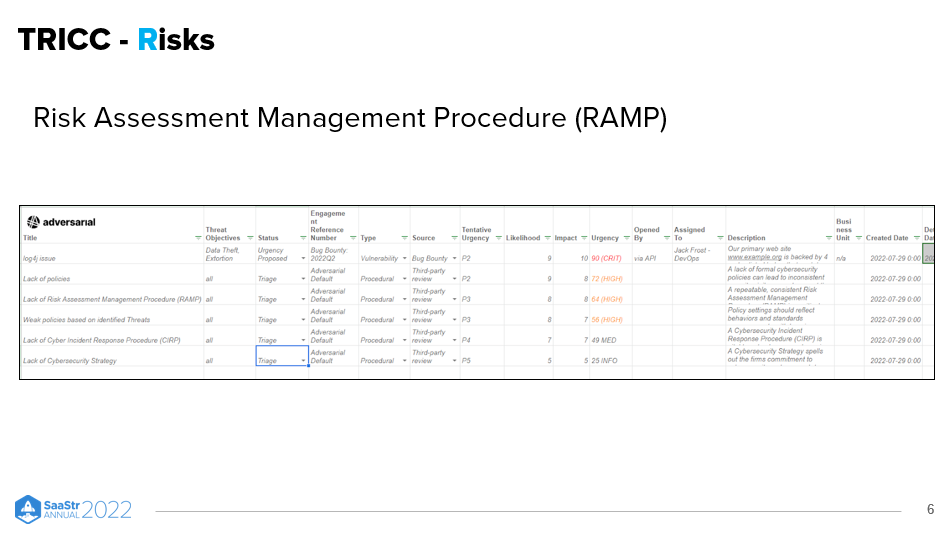
Cybersecurity risks can come in many forms. But it’s essential to develop a risk register that’s also tool-agnostic. You want to build a sense of your potential dangers that don’t end up locking you into a particular cybersecurity tool. Take care to define your concerns so you don’t buy the wrong tool to combat them.
Incidents: Cyber Incident Response Procedure (CIRP)
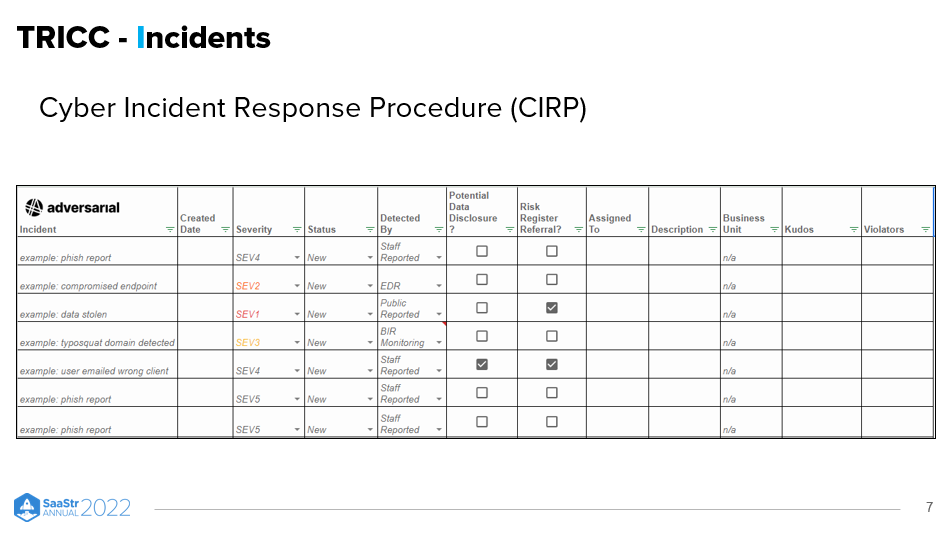
Similar to Risks, the goal of adhering to the CIRP is to develop a standard approach so that you can assess any occurrences with the same vocabulary. When compliance or regulatory officers enquire about whether you’ve had any incidents, you can have a clear answer and record to give them.
Controls

Once you’ve defined your ongoing projects in response to the risk register, how can you assess your progress? However, this can be as simple as using the traffic light system: green for good, amber for caution, and red for danger.
Compliance
Anyone in charge of customer data knows compliance can feel incredibly daunting. But if you’ve done everything above, you’ll soon find that tasks like SOC 2 (voluntary audits that can demonstrate that you securely manage your data) and third-party risk management (TPRM) become common sense.
Key Takeaways
- Start Early. Consider your security from day one. If you wait too long and potential clients have questions about your security, you may fall short when trying to close a deal.
- Don’t Wait for a CISO. Even if you don’t have or hesitate to pay for quality expertise, set up a Cybersecurity & Privacy Governance committee and use the TRICC framework to build a foundation for understanding your risks.
- Secure Compliance. If you’ve done the legwork to secure your company and assets, you’ll be amazed at how much easier compliance can be.
The post How to Know When It’s Time to Hire a CISO with Adversarial Risk Management Founder Jerry Perullo and SafeBase Director of Strategy and Operations Macy Mody (Video) appeared first on SaaStr.
via https://www.aiupnow.com
Amanda Beaty, Khareem Sudlow
